Unsupported public key authentication algorithm SshRsa (ssh-rsa)? Here's how to fix it.
As every good System Administrator already knows, an extremely interesting research paper published in 2023 by Keegan Ryan, Kaiwen He, George A. Sullivan, and Nadia Heninger, mathematically proved yet another weakness with RSA keys, which are often used as host keys by/for SSH/SFTP servers, or to authenticate SSH users via PKI.
For such reason, starting from Syncplify Server! v6.2.26 the ssh-rsa algorithm is no longer among the default active ones. Please understand that we have done so to protect our customers and users and ensure that we can keep the reputation we earned in the last decade as the only enterprise-grade SSH/SFTP server on the market that's never been hacked.
Yet, more often than we thought, we receive emails and support tickets informing us that some SSH/SFTP clients attempting to connect to our server software are receiving an error message like this: "Unsupported public key authentication algorithm SshRsa (ssh-rsa)". So, what to do about it?
Well, there are two roads you can follow, one that is formally and actually correct and ensures your server's safety and security, and one that works but weakens the overall safety and security of your server for every one of your users. Let's explore them both.
The correct way to fix this
The only correct way to fix this is to ditch RSA keys completely. They should appear absolutely nowhere in your server's configuration, no RSA host key, no RSA keys to authenticate your users, and no ssh-rsa host-key or PKI algorithm enabled. Then configure all of your clients to use alternative algorithms (Ed25519 is strongly recommended) when they connect to your server. Yes, it's a hassle and it requires a lot of reconfigurations of a lot of moving parts, but no effort is too big compared to the cost (legal, monetary, and material) of being hacked.
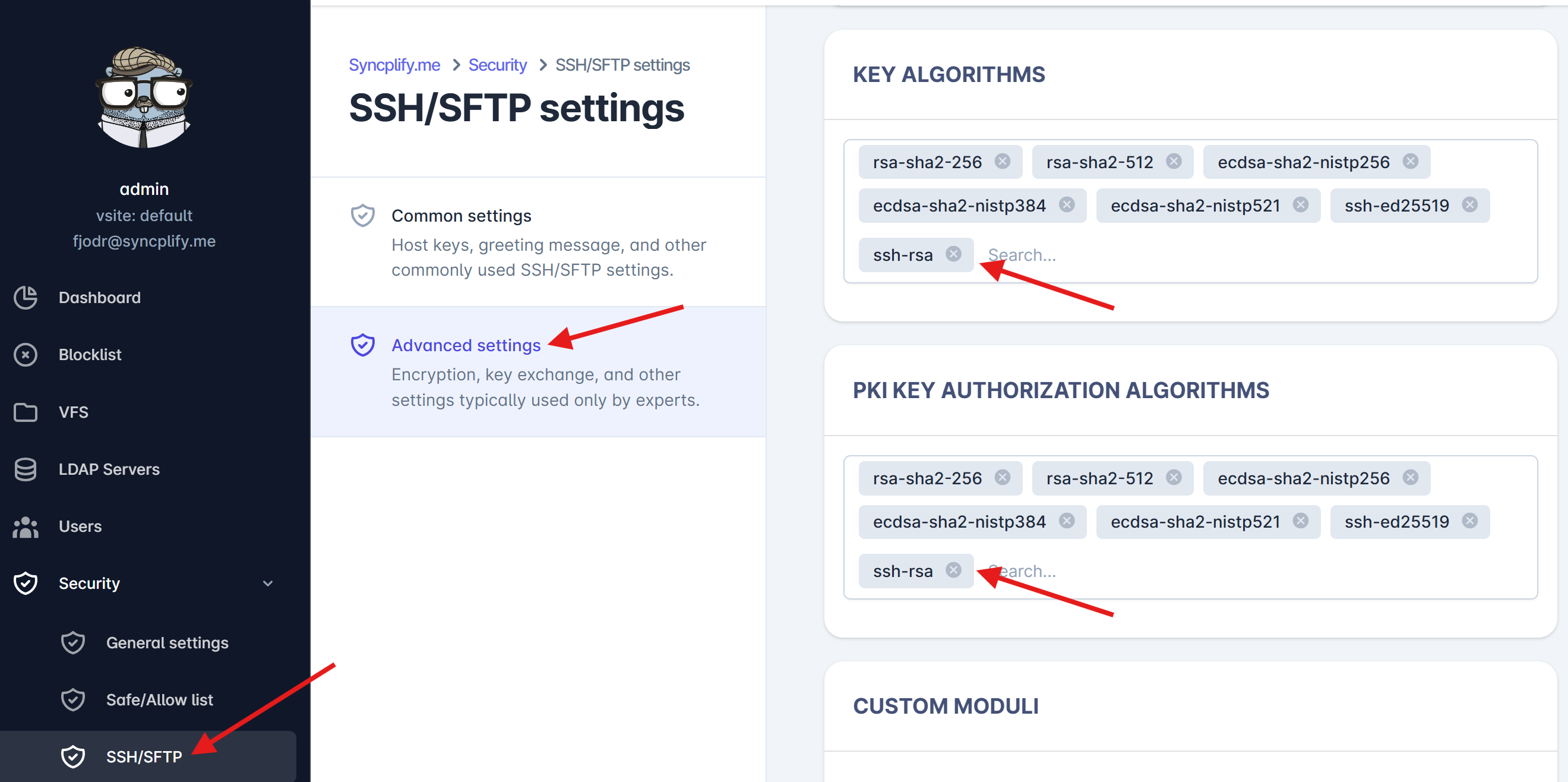
The quick-and-dirty (and insecure) way to fix this
You can, of course, keep your RSA keys (host key and user keys) and enable the ssh-rsa algorithm in your server as shown in the screenshot here below:
Please keep in mind that any change to the security algorithms of your SSH/SFTP server will only take effect after you restart your Virtual Site from the SuperAdmin UI.
WARNING: please be aware that if you choose this second (quick-and-dirty and insecure) option, against our advice and recommendations, Syncplify won't be liable in any way if and when your SSH/SFTP server is hacked.